文章目录
1 远程管理服务
—1.1 SSH方式
yum install -y openssh*
b SSH服务端口信息: 22
c SSH服务更加安全: 会对数据信息进行加密
d SSH服务应用: 远程连接(外网) 远程复制(scp) 远程共享数据存储(sftp)
[root@web01 ~]# ssh 10.0.0.31
root@10.0.0.31's password:
Last login: Tue May 16 12:55:48 2023 from 10.0.0.1
[root@nfs01 ~]# logout
Connection to 10.0.0.31 closed.
[root@web01 ~]# slogin 10.0.0.31
root@10.0.0.31's password:
Last login: Tue May 16 13:10:01 2023 from 10.0.0.7
[root@nfs01 ~]#
—1.2 telnet方式
(telnet无法实现root用户远程登陆)
[root@nfs01 data]#yum install -y telnet*
[root@nfs01 data]# yum install net-tools
[root@nfs01 data]# netstat -lntup|grep 23
tcp6 0 0 :::23 :::* LISTEN 1/systemd
[root@web01 ~]# telnet 10.0.0.31
nfs01 login: oldboy
Password:
Last login: Thu Apr 13 06:58:43 on pts/0
[oldboy@nfs01 ~]$su - root
[root@nfs01 ~]#
telnet服务端口信息: 23
telnet服务不够安全: 不会对数据进行进行加密(明文)
telnet服务应用: 远程连接(内部) 用于测试
2 SSH远程服务信息说明
[root@nfs01 ~]# rpm -ql openssh-clients
/etc/ssh/ssh_config --- SSH客户端配置
/usr/bin/scp --- 远程传输数据命令
/usr/bin/sftp --- 远程传输数据(ftp方式)
/usr/bin/slogin --- 远程连接登陆命令
/usr/bin/ssh --- 远程连接登陆命令
/usr/bin/ssh-copy-id --- 非常重要的命令(分发公钥信息)
/usr/bin/ssh-add
/usr/bin/ssh-agent
/usr/bin/ssh-keyscan
[root@nfs01 ~]# rpm -ql openssh-server
/etc/ssh/sshd_config --- SSH服务端配置文件
/usr/sbin/sshd --- SSH服务启动进程命令
/usr/sbin/ssh-keygen --- 创建密钥信息(私钥和公钥)
让服务命令在后台运行
a /usr/sbin/sshd -D &
nohup /usr/sbin/sshd -D &(关闭会话连接也后台运行)
jobs查看后台命令--> fg 编号(将进程在前台显示了)
[root@web01 ~]# systemctl stop sshd
[root@web01 ~]# /usr/sbin/sshd -D &
[1] 9991
[root@web01 ~]# jobs
[1]+ Running /usr/sbin/sshd -D &
[root@web01 ~]# fg 1
/usr/sbin/sshd -D
3 SSH远程连接口令连接原理
01. 执行远程连接命令
ssh 172.16.1.7
02. 确认连接信息(客户端进行确认)
03. 输入密码信息, 认证通过
04. 发送公钥信息(服务端发送公钥信息)
05. 连接成功
06. 断开连接重新连接
07. 会完成客户端公钥和服务端私钥进行匹配流程
08. 直接输入密码信息,登陆成功
[root@nfs01 ~]# ssh 10.0.0.7
The authenticity of host '10.0.0.7 (10.0.0.7)' can't be established.
ECDSA key fingerprint is SHA256:QeCOyADOMwjW7dzC+rHHoLHXJIg1FXgKU3zuyLN+bVs.
ECDSA key fingerprint is MD5:e4:32:6a:5b:d9:2a:94:51:98:0d:7b:2f:02:e5:d6:29.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.0.0.7' (ECDSA) to the list of known hosts.
root@10.0.0.7's password:
Last login: Tue May 16 18:13:17 2023 from 10.0.0.1
[root@web01 ~]# logout
Connection to 10.0.0.7 closed.
[root@nfs01 ~]# cat ./.ssh/known_hosts
10.0.0.7 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOUcKmG/VKwy2XkeSq4eSrjDOifWaqI5cM5DsOxWX9tN+4xMOw/ygvO1b85DXOA+SjhMqrdFpbrbIyBz136jJlw=
[root@web01 ~]# cat /etc/ssh/ssh_host_ecdsa_key.pub
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOUcKmG/VKwy2XkeSq4eSrjDOifWaqI5cM5DsOxWX9tN+4xMOw/ygvO1b85DXOA+SjhMqrdFpbrbIyBz136jJlw=
[root@web01 ~]# ll /etc/ssh/
total 604
-rw-r--r-- 1 root root 581843 Nov 25 2021 moduli
-rw-r--r-- 1 root root 2276 Nov 25 2021 ssh_config
-rw------- 1 root root 3905 May 3 13:59 sshd_config
-rw-r-----. 1 root ssh_keys 227 Jan 31 01:58 ssh_host_ecdsa_key
-rw-r--r--. 1 root root 162 Jan 31 01:58 ssh_host_ecdsa_key.pub
-rw-r-----. 1 root ssh_keys 387 Jan 31 01:58 ssh_host_ed25519_key
-rw-r--r--. 1 root root 82 Jan 31 01:58 ssh_host_ed25519_key.pub
-rw-r-----. 1 root ssh_keys 1679 Jan 31 01:58 ssh_host_rsa_key
-rw-r--r--. 1 root root 382 Jan 31 01:58 ssh_host_rsa_key.pub
[root@nfs01 ~]# rpm -ql openssh-clients /etc/ssh/ssh_config --- SSH客户端配置 /usr/bin/scp --- 远程传输数据命令 /usr/bin/sftp --- 远程传输数据(ftp方式) /usr/bin/slogin --- 远程连接登陆命令 /usr/bin/ssh --- 远程连接登陆命令 /usr/bin/ssh-copy-id --- 非常重要的命令(分发公钥信息) /usr/bin/ssh-add /usr/bin/ssh-agent /usr/bin/ssh-keyscan [root@nfs01 ~]# rpm -ql openssh-server /etc/ssh/sshd_config --- SSH服务端配置文件 /usr/sbin/sshd --- SSH服务启动进程命令 /usr/sbin/ssh-keygen --- 创建密钥信息(私钥和公钥) 让服务命令在后台运行 a /usr/sbin/sshd -D & nohup /usr/sbin/sshd -D &(关闭会话连接也后台运行) jobs查看后台命令--> fg 编号(将进程在前台显示了) [root@web01 ~]# systemctl stop sshd [root@web01 ~]# /usr/sbin/sshd -D & [1] 9991 [root@web01 ~]# jobs [1]+ Running /usr/sbin/sshd -D & [root@web01 ~]# fg 1 /usr/sbin/sshd -D
3 SSH远程连接口令连接原理
01. 执行远程连接命令
ssh 172.16.1.7
02. 确认连接信息(客户端进行确认)
03. 输入密码信息, 认证通过
04. 发送公钥信息(服务端发送公钥信息)
05. 连接成功
06. 断开连接重新连接
07. 会完成客户端公钥和服务端私钥进行匹配流程
08. 直接输入密码信息,登陆成功
[root@nfs01 ~]# ssh 10.0.0.7
The authenticity of host '10.0.0.7 (10.0.0.7)' can't be established.
ECDSA key fingerprint is SHA256:QeCOyADOMwjW7dzC+rHHoLHXJIg1FXgKU3zuyLN+bVs.
ECDSA key fingerprint is MD5:e4:32:6a:5b:d9:2a:94:51:98:0d:7b:2f:02:e5:d6:29.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.0.0.7' (ECDSA) to the list of known hosts.
root@10.0.0.7's password:
Last login: Tue May 16 18:13:17 2023 from 10.0.0.1
[root@web01 ~]# logout
Connection to 10.0.0.7 closed.
[root@nfs01 ~]# cat ./.ssh/known_hosts
10.0.0.7 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOUcKmG/VKwy2XkeSq4eSrjDOifWaqI5cM5DsOxWX9tN+4xMOw/ygvO1b85DXOA+SjhMqrdFpbrbIyBz136jJlw=
[root@web01 ~]# cat /etc/ssh/ssh_host_ecdsa_key.pub
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOUcKmG/VKwy2XkeSq4eSrjDOifWaqI5cM5DsOxWX9tN+4xMOw/ygvO1b85DXOA+SjhMqrdFpbrbIyBz136jJlw=
[root@web01 ~]# ll /etc/ssh/
total 604
-rw-r--r-- 1 root root 581843 Nov 25 2021 moduli
-rw-r--r-- 1 root root 2276 Nov 25 2021 ssh_config
-rw------- 1 root root 3905 May 3 13:59 sshd_config
-rw-r-----. 1 root ssh_keys 227 Jan 31 01:58 ssh_host_ecdsa_key
-rw-r--r--. 1 root root 162 Jan 31 01:58 ssh_host_ecdsa_key.pub
-rw-r-----. 1 root ssh_keys 387 Jan 31 01:58 ssh_host_ed25519_key
-rw-r--r--. 1 root root 82 Jan 31 01:58 ssh_host_ed25519_key.pub
-rw-r-----. 1 root ssh_keys 1679 Jan 31 01:58 ssh_host_rsa_key
-rw-r--r--. 1 root root 382 Jan 31 01:58 ssh_host_rsa_key.pub
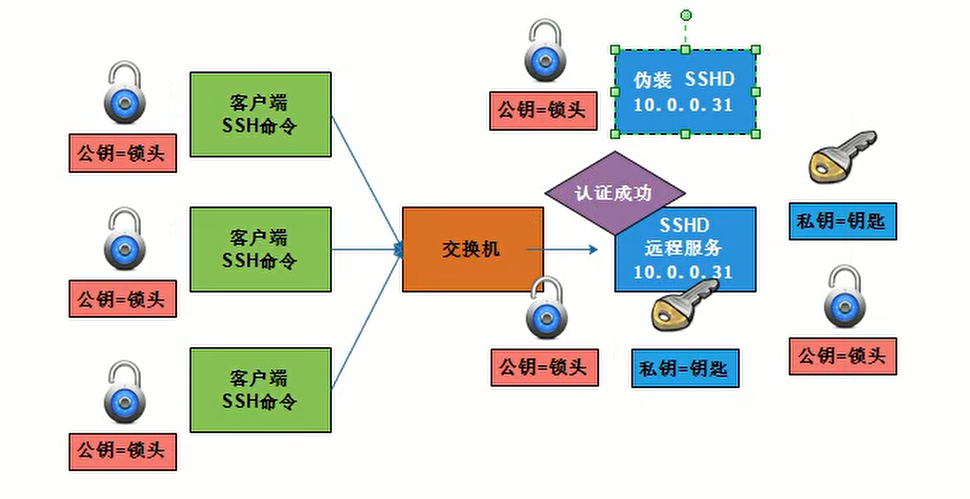
4 SSH远程连接密钥连接原理
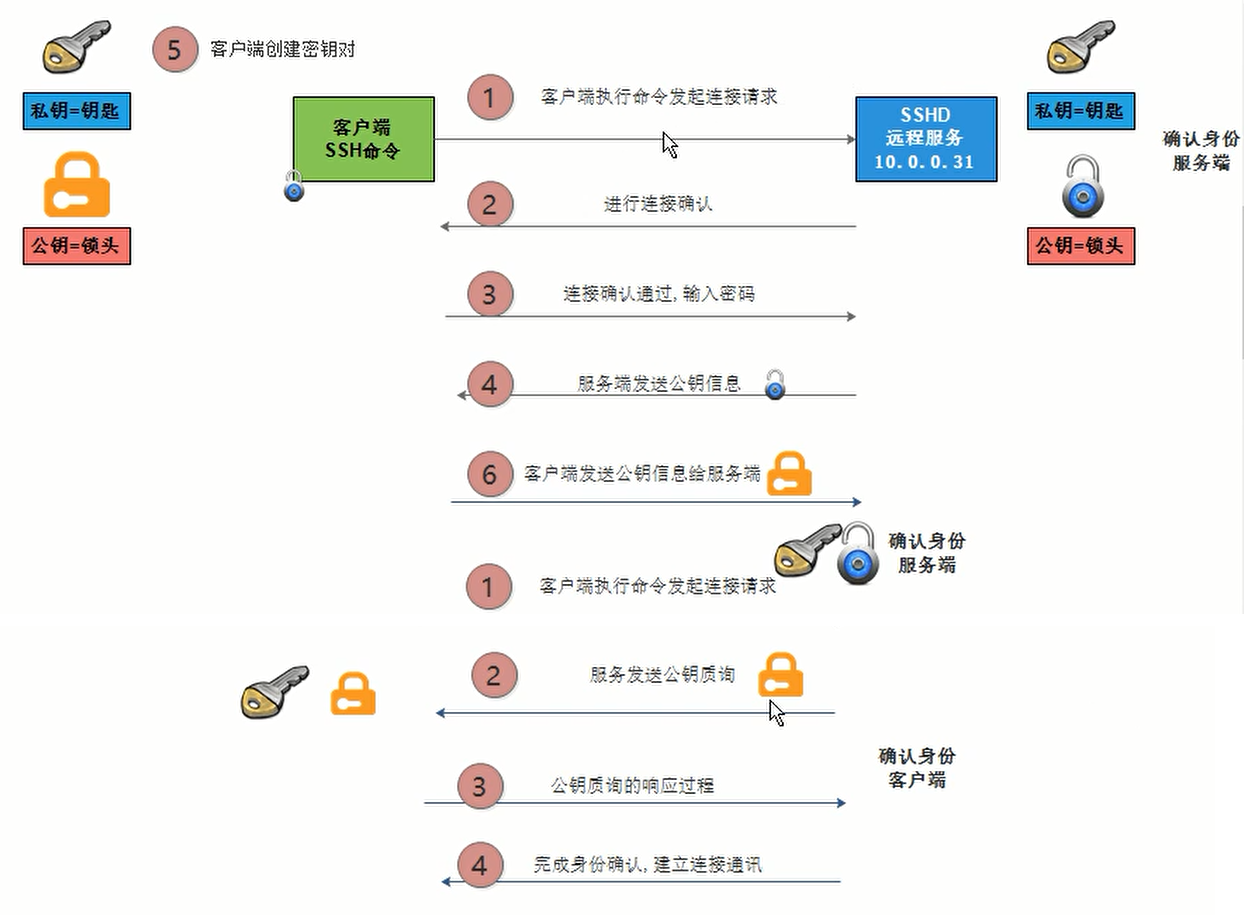
5 SSH免密码登陆部署方式
—5.1 客户端创建密钥对信息
管理主机10.0.0.61
[root@m01 ~]# ssh-keygen -t dsa
Generating public/private dsa key pair.
Enter file in which to save the key (/root/.ssh/id_dsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_dsa.
Your public key has been saved in /root/.ssh/id_dsa.pub.
The key fingerprint is:
SHA256:2B/yt+K0ioZacah23kGwjbl7R4mRHZ06pwaP5iEHBVk root@m01
The key's randomart image is:
+---[DSA 1024]----+
| .+E . . |
| . . . o |
| .. o o |
| .B+o+ . |
| *.=*S=. |
| ..=* *+ . |
| o +*.+ + . |
| . +.o+o...o . |
| ..ooo..oo.. |
+----[SHA256]-----+
[root@m01 ~]# ll ~/.ssh/
total 8
-rw------- 1 root root 668 Mar 4 10:36 id_dsa
-rw-r--r-- 1 root root 598 Mar 4 10:36 id_dsa.pub
—5.2 分发公钥信息
[root@m01 ~]# ssh-copy-id -i ~/.ssh/id_dsa.pub root@172.16.1.31
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_dsa.pub"
The authenticity of host '172.16.1.31 (172.16.1.31)' can't be established.
ECDSA key fingerprint is SHA256:QFkTlov1H4MLKN0wlrj/Tlc9nL9ResNI7Eqbw1ZYkH0.
ECDSA key fingerprint is MD5:01:85:0c:25:e2:cf:66:10:55:26:68:97:10:0f:a8:9f.
Are you sure you want to continue connecting (yes/no)? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@172.16.1.31's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@172.16.1.31'"
and check to make sure that only the key(s) you wanted were added.
说明: 默认第一个分发公钥,需要基于口令方式建立连接
[root@m01 ~]# cat ./.ssh/id_dsa.pub
ssh-dss AAAAB3NzaC1kc3MAAACBAOBUaY3ZlKNDwOiL45392YP1LUzT3VtVqkkYJuqD7x/y0eNnF/J588tsinSfrjtlYplGqLHdDsp65e7B/1NUOijypKWeTkIX6UI7z/PDbJeD8gTZOolGDyFB9pkweIuSc+gDPzLMmTVxJGhh+Jb9wMy4E9FMgk60bEhwqJk6oeb/AAAAFQD4Oxfol5kEtiFvrnhEUg9SBmHamwAAAIBzgidCC9Rp2Esr6DwITX4nB6uVCTQBCUFfD5U6kDohGx6BO9gbYl7u7ZQTQXLHEJXb5SVQpPb/UNLt1B9Yv4xmDNM1BJ0o9g9XQo9LMSydthl3Ud8j1Qf38O8GD9Gn6marnRPU34YI7NCjJUA/orInn4dN+xhc2biiyOfv/JsZUAAAAIEAgq8q5AYNjhj9b6MSkF9IQkLSv0cch7Tsbyuj+NOzrOKkrqegyfNVVj25Q4+fWLn11W6ZCjeaAVNebdAzhNsRIYRIdiEQzSB/FTtDzQmrFdBG1NxwtQhguBGm7sh740K1ABsT0rk5pOEzrfsZN3mv8MIe01S9G+xKAdyv/NXp160= root@m01
[root@nfs01 ~]# cat ~/.ssh/authorized_keys
ssh-dss AAAAB3NzaC1kc3MAAACBAOBUaY3ZlKNDwOiL45392YP1LUzT3VtVqkkYJuqD7x/y0eNnF/J588tsinSfrjtlYplGqLHdDsp65e7B/1NUOijypKWeTkIX6UI7z/PDbJeD8gTZOolGDyFB9pkweIuSc+gDPzLMmTVxJGhh+Jb9wMy4E9FMgk60bEhwqJk6oeb/AAAAFQD4Oxfol5kEtiFvrnhEUg9SBmHamwAAAIBzgidCC9Rp2Esr6DwITX4nB6uVCTQBCUFfD5U6kDohGx6BO9gbYl7u7ZQTQXLHEJXb5SVQpPb/UNLt1B9Yv4xmDNM1BJ0o9g9XQo9LMSydthl3Ud8j1Qf38O8GD9Gn6marnRPU34YI7NCjJUA/orInn4dN+xhc2biiyOfv/JsZUAAAAIEAgq8q5AYNjhj9b6MSkF9IQkLSv0cch7Tsbyuj+NOzrOKkrqegyfNVVj25Q4+fWLn11W6ZCjeaAVNebdAzhNsRIYRIdiEQzSB/FTtDzQmrFdBG1NxwtQhguBGm7sh740K1ABsT0rk5pOEzrfsZN3mv8MIe01S9G+xKAdyv/NXp160= root@m01
—5.3 连接测试
[root@m01 ~]# ssh 10.0.0.31
Last login: Tue May 16 19:02:36 2023 from 10.0.0.61
[root@nfs01 ~]# clear
[root@nfs01 ~]# logout
Connection to 10.0.0.31 closed.
[root@m01 ~]# clear
[root@m01 ~]# ssh 10.0.0.31 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:7d:77:4f brd ff:ff:ff:ff:ff:ff
inet 10.0.0.31/24 brd 10.0.0.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe7d:774f/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:7d:77:59 brd ff:ff:ff:ff:ff:ff
inet 172.16.1.31/24 brd 172.16.1.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe7d:7759/64 scope link
valid_lft forever preferred_lft forever
问题一: 如何批量分发公钥
基于脚本循环
问题二: 如何SSH服务端口号变更如何进行分发
基于特殊参数
6 编写SSH配置文件
vim /etc/ssh/sshd_config
#Port 22 --- 修改服务端口号参数
#ListenAddress 0.0.0.0 --- 修改监听地址(指定的监听地址可以建立连接)
0.0.0.0监听本地主机网卡有的所有地址, 建议只监听内网网卡地址
172.16.1.31 服务只能监听本地网卡上有的地址
[root@nfs01 ~]# cat /etc/ssh/sshd_config
[root@m01 ~]# ssh 172.16.1.31
Last login: Tue May 16 20:39:34 2023 from 10.0.0.61
[root@nfs01 ~]# logout
Connection to 172.16.1.31 closed.
[root@m01 ~]# ssh 10.0.0.31
ssh: connect to host 10.0.0.31 port 22: Connection refused
#PermitEmptyPasswords no --- 是否允许空密码登陆连接,默认不允许
#PermitRootLogin yes --- 是否允许root用户远程登陆,默认允许
GSSAPIAuthentication no --- 特殊的认证需要关闭(提升远程连接效率)
#UseDNS no --- 开启了代表具有DNS反向解析功能
DNS正向解析: 已知域名信息得到IP地址信息
DNS反向解析: 已知IP信息得到获得域名信息
(需要以来hosts文件配置,如果文件没有配置,反向解析过程会影响远程连接效率)
7 批量分发公钥/批量验证
—7.1 批量分发公钥问题汇总
问题一:利用脚本循环操作
mkdir /server/scripts -p
vim fenfa.sh --- 初始分发公钥脚本
#!/bin/bash
for ip in `cat /server/scripts/ip_list.txt`
do
ssh-copy-id -i /root/.ssh/id_dsa.pub root@$ip
done
问题二: 分发时不用输入密码
yum install -y sshpass
sshpass -p123456 ssh-copy-id -i ~/.ssh/id_dsa.pub root@172.16.1.31
问题三: 分发时不用进行确认(yes/no)
[root@backup ~]# rm -rf ./.ssh/authorized_keys
[root@m01 scripts]# >~/.ssh/known_hosts 为了实现确认效果,需要清除客户端known_hosts文件
[root@m01 scripts]# sshpass -p123456 ssh-copy-id -i ~/.ssh/id_dsa.pub root@172.16.1.31 -o StrictHostKeyChecking=no
问题四: $?指检验最近的一次命令是否执行成功,成功输出值为0
[root@m01 scripts]# echo $?
0
[root@m01 scripts]# sshpass -p12345846 ssh-copy-id -i ~/.ssh/id_dsa.pub root@172.16.1.31
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_dsa.pub"
[root@m01 scripts]# echo $?
6
[root@m01 scri
问题五: 脚本成功失败提醒
[root@m01 scripts]# source /etc/init.d/functions
[root@m01 scripts]# action "start fail" /bin/false
start fail [FAILED]
[root@m01 scripts]# vim fenfa_pub.sh
[root@m01 scripts]# action "fail" /bin/false
fail [FAILED]
[root@m01 scripts]# action "success" /bin/true
success [ OK ]
问题六: 如何SSH服务端口号变更如何进行分发 基于特殊参数
ssh-copy-id -i ~/.ssh/id_dsa.pub root@172.16.1.31 -p52113
—7.2 批量分发公钥脚本
[root@m01 scripts]# cat fenfa_pub.sh
#!/bin/bash
source /etc/init.d/functions
for ip in `cat /server/scripts/ip_list.txt`
do
sshpass -p123456 ssh-copy-id -i ~/.ssh/id_dsa.pub root@$ip -o StrictHostKeyChecking=no &>/dev/null
if [ $? -ne 0 ]
then
action "host $ip 分发失败" /bin/false
else
action "host $ip 分发成功" /bin/true
fi
done
[root@m01 scripts]# sh fenfa_pub.sh
host 172.16.1.31 分发成功 [ OK ]
host 172.16.1.41 分发成功 [ OK ]
host 172.16.1.7 分发成功 [ OK ]
—7.3 分发测试检查脚本
#!/bin/bash
source /etc/init.d/functions
if [ $# -ne 1 ]
then
echo "执行脚本时,请添加加hostname等命令参数"
exit
fi
for ip in `cat /server/scripts/ip_list.txt`
do
ssh root@$ip $1
if [ $? -ne 0 ]
then
action "host $ip 检查分发失败!" /bin/false
else
action "host $ip 检查分发成功 !" /bin/true
fi
echo ""
done
vim /etc/ssh/sshd_config #Port 22 --- 修改服务端口号参数 #ListenAddress 0.0.0.0 --- 修改监听地址(指定的监听地址可以建立连接) 0.0.0.0监听本地主机网卡有的所有地址, 建议只监听内网网卡地址 172.16.1.31 服务只能监听本地网卡上有的地址 [root@nfs01 ~]# cat /etc/ssh/sshd_config [root@m01 ~]# ssh 172.16.1.31 Last login: Tue May 16 20:39:34 2023 from 10.0.0.61 [root@nfs01 ~]# logout Connection to 172.16.1.31 closed. [root@m01 ~]# ssh 10.0.0.31 ssh: connect to host 10.0.0.31 port 22: Connection refused #PermitEmptyPasswords no --- 是否允许空密码登陆连接,默认不允许 #PermitRootLogin yes --- 是否允许root用户远程登陆,默认允许 GSSAPIAuthentication no --- 特殊的认证需要关闭(提升远程连接效率) #UseDNS no --- 开启了代表具有DNS反向解析功能 DNS正向解析: 已知域名信息得到IP地址信息 DNS反向解析: 已知IP信息得到获得域名信息 (需要以来hosts文件配置,如果文件没有配置,反向解析过程会影响远程连接效率)
 MySQL学习笔记
MySQL学习笔记